26/01: Security Layers Model
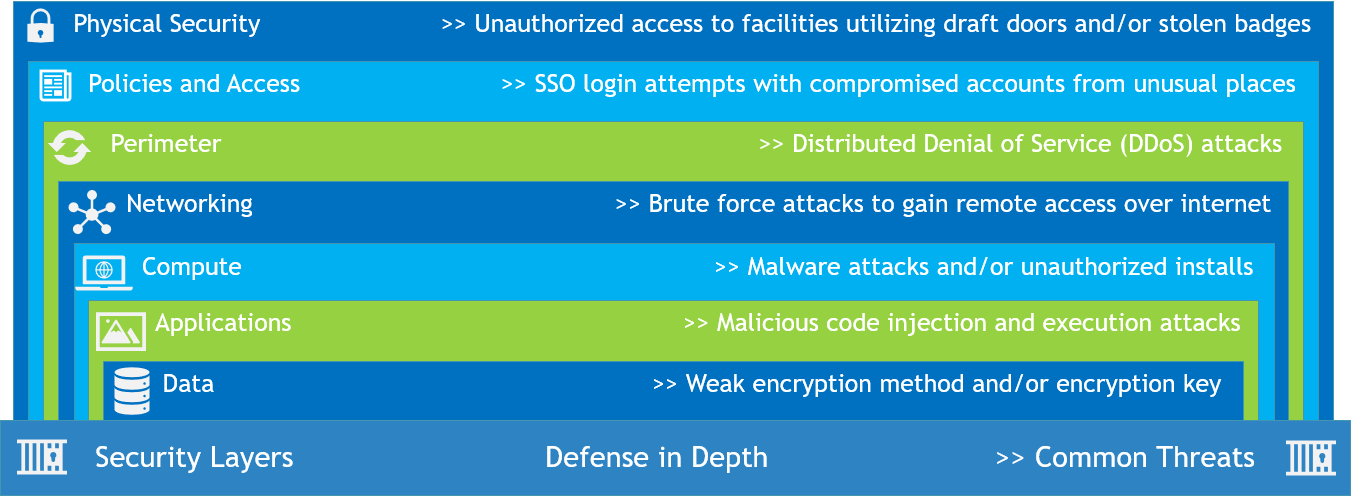
The Security Solution needs to account for the solutions for each layer described in the diagram. In specialized cases, one can assume risk but in most use cases, one should identify and implement solutions for the common threats to complete the security solution. Defense in depth is all about having security protection at multiple layers. The Security Model can serve as the point of reference when we are working on the Security Solution Design.

Disclaimer
The thoughts expressed in the blog are those of the author and do not represent necessarily the official policy or position of any other agency, organization, employer, or company. Assumptions made in the study are not reflective of the point of view(s) of any entity other than the author. Since we are critically thinking human beings, the point of view(s) is always subject to change, revision and rethinking at any time. While reasonable efforts have been made to obtain accurate information, the author makes no warranty, expressed or implied as to its accuracy.
The thoughts expressed in the blog are those of the author and do not represent necessarily the official policy or position of any other agency, organization, employer, or company. Assumptions made in the study are not reflective of the point of view(s) of any entity other than the author. Since we are critically thinking human beings, the point of view(s) is always subject to change, revision and rethinking at any time. While reasonable efforts have been made to obtain accurate information, the author makes no warranty, expressed or implied as to its accuracy.
