Shortly after earning a Master of Science in Operations Research and Statistics at the Indian Institute of Technology (IIT Bombay), I joined as a Research Scientist in the Artificial Intelligence Lab for the Computer Science Department. I developed an AI application for routing and scheduling crews that delivered operations efficiency of 36% for our customers and won numerous awards and national recognition.
Later, moving to the United States, I worked as a Software Engineer with companies such as AT&T and IBM. One key highlight was developing security architecture for single sign-on for over 200 mission-critical apps at AT&T. It was followed by a stint with NLM, where I delivered Data Integration between the NLM and FDA, Search Engine, and Conversational AI for self-service.
Next, I worked at Aol as an Operations Architect, a key role in enabling billing and subscription services and setting up enterprise standards and best practices. While at Aol, I earned a Master of Science in Technology Management at George Mason University and a Chief Information Officer Certificate at United States Federal CIO University.
Over the last ten years, I have led consulting, solution center, and pre-sales at SRA International / General Dynamics Information Technology, CenturyLink / Savvis / Lumen, and IBM / Kyndryl. Notable Accomplishments in Apps and Data Space:
- SRA International / General Dynamics Information Technology: Executed the modernization of the Centers for Disease Control and Prevention's vaccine adverse event reporting system (The Largest Program in the World) to enable self-service and green initiatives to deliver digital reporting and remote work options.
- IBM / Kyndryl: Onboarded a large new logo client in the insurance industry to adopt Hybrid Cloud, DevOps, and API-driven managed services to deliver on-demand one-click Guidewire Apps environments, reducing the environment delivery timeline from 45 days to 8 hours.
- Kyndryl: Developed an advanced Banking Payments Ecosystem Transaction Logs Data Mining Tool using Python. This efficient tool enables platform engineering and operations teams to accurately predict transaction performance while providing valuable recommendations for optimizing the ecosystem.
I have co-founded:
Learn more about me:
05/09: Resume
JASWANT SINGH
Email: [email protected]
Text / Voice / WhatsApp: 703.662.1097
US Citizen Security Clearance: POT 6C
Reston, Virginia
APPS, DATA, CLOUD, and INTEGRATION TECHNOLOGY EXECUTIVE
My Blog: https://techblog.baghel.com
LinkedIn: https://www.linkedin.com/in/jaswantsingh
Email: [email protected]
Text / Voice / WhatsApp: 703.662.1097
US Citizen Security Clearance: POT 6C
Reston, Virginia
APPS, DATA, CLOUD, and INTEGRATION TECHNOLOGY EXECUTIVE
My Blog: https://techblog.baghel.com
LinkedIn: https://www.linkedin.com/in/jaswantsingh
EXECUTIVE SUMMARY
Experienced Apps, Data, Cloud, and Integration Executive with over 25 years of driving digital transformation for Fortune 500 companies, generating over $960 million in global revenue through Azure, AWS, GCP, OCI, IBM Cloud, VMware, and Red Hat from ideation to launch.
KEY ACCOMPLISHMENTS
- Cloud Computing Evangelist: Delivered keynote on SaaS best practices at SaaSCon, SantaClara, California, and developed a Cloud Adoption Strategy framework for hybrid IT, accelerating enterprise modernizations.
- Data, AI & ML Platform Leader: Headed Big Data practice at CenturyLink, delivering strategy, implementation, and managed services that drove growth for financial services and omnichannel retail clients.
- Site Reliability & DevSecOps: Deployed enterprise SOA and led DevSecOps for billing and subscription applications at Aol, improving agility and operational efficiency.
CORE COMPETENCIES
- Leadership: Global team management, coaching/mentoring, enterprise architecture, P&L oversight, financial engineering, analytical problem-solving.
- Data & Cloud: Data ecosystems (democratization, architectures: Warehouse / Lake / Lakehouse / DataMart / Mesh; security, hubs, fabrics); Multi-cloud mastery (Azure, AWS, GCP, OCI, IBM Cloud, VMware, OpenShift) across SaaS / PaaS / CaaS / IaaS / Serverless / Cloud-Native.
- Apps & Automation: App / software / system / infra implementation / rationalization / modernization / migration; CI/CD pipelines, DevSecOps, service / resource automation, IaC.
PROFESSIONAL EXPERIENCE
Kyndryl / IBM, Dulles, Virginia
JUNE 2018 - PRESENT
Director - Innovation and Integration, Global Cloud Practice; Client Technical Leader, US Financial Services; Chief Enterprise Architect, US CTO Office
- Provided C-level advisory and thought leadership for Digital Transformation and IT Outsourcing, co-creating enterprise solutions that generated over $360M in revenue.
- Developed framework for assessing application portfolios to create cloud disposition plans, roadmaps, and business opportunities.
- Designed and delivered industry-first cloud-native solutions for banking branch technology using NG One, Splunk, and Azure Cloud, enabling centralized management of banking branch peripherals for deployment and operations.
- Led the largest U.S. Guidewire Hybrid Cloud and DevSecOps implementation, delivering one-click API-driven environments that cut delivery timelines from 45 days to 8 hours.
- Developed a Python-based Banking Payments Ecosystem Transaction Logs Data Mining Tool, enabling platform engineering and operations teams to provide optimization recommendations and predict transaction performance.
Lumen Technologies / CenturyLink, Dulles, Virginia
OCTOBER 2011 - MAY 2018
Senior Director - Global Advanced Services Solution Center; Principal Enterprise Architect, Consulting and Implementation Services
- Directed cross-organization matrix teams for multimillion-dollar solutions in Applications and Infrastructure Rationalization, Modernization and Migration, Data Center Migration and Consolidation, and Business Resiliency. Created Cloud Readiness Assessment and Big Data Practice, driving Digital Transformation opportunities.
- Led strategic deal pursuits and onboarded new clients with 100% success rate; built and managed high-performing team of solutions architects, generating over $600M in revenue through global enterprise digital transformations.
Previous Professional Experience
JULY 1995 - OCTOBER 2011
Pioneered cloud and SOA architectures, operationalized billing systems, architected federal health applications, co-founded technology ventures, and advanced AI research for enterprise excellence.
- Chief Architect - Cloud and Service-Oriented Architecture (SOA) Center of Excellence, SRA International / General Dynamics Information Technology Inc.
- Operations Architect - Billing and Subscription, and Web and Java Center of Excellence,America Online (AOL Inc.).
- Software Architect - Applications Branch, Office of Computer and Communications Systems (OCCS), US National Library of Medicine / Lockheed Martin.
- Co-Founder and Chief Technology Officer, StrategiesTool, Suchna! / Baghel Corporation.
- Senior Software Engineer - Interactive Advantage, AT&T / IBM Global Services.
- Research Scientist and Founding Member, Mumbai Educational Trustís Institute of Software Development and Research.
- Research Scientist - Management of Informatics and Technology for Enterprise Excellence (MINT-EX), Artificial Intelligence Research Lab, Indian Institute of Technology Bombay.
PUBLICATIONS
- Cloud Migration & Modernization Solution Design Options, and Industry Leading Practices, Microsoft Azure Architect Technologies & Design, Presented at IBM Your Learning
- Getting Started with Oracle SOA BPEL Process Manager, Packt Publishing, ISBN 978-1-84968-898-7
- Best Practices for Developing & Deploying SaaS, White Paper, Presented at SaaSCon, Santa Clara, California
- Web Application Security Implementation and Industry Best Practices Handbook, Presented at SRA University
EDUCATION
- United States Federal CIO University
CIO University Certificate, Federal Executive Competencies - Costello College of Business, George Mason University, Virginia
Master of Science in Technology Management - Department of Mathematics, Indian Institute of Technology Bombay
Master of Science in Mathematics, Specialization in Operations Research and Statistics
Introduction
Enterprise Applications Rationalization is a process to create business-driven application system architecture. That demands continuous input and collaboration across business, technology, and operations. We often find that enterprises lack support from business owners for the Enterprise Applications Rationalization. The Applications Disposition Strategy from applications architectures and runtimes only is a recipe for disaster down the line.
So What?
Enterprise Applications Rationalization is the mission-critical journey for any enterprise. Not doing it can put an enterprise in the same boat as Aol and Yahoo in a matter of time. The III-Phase approach enables an enterprise to stay relevant in the marketplace with the end-to-end alignment from a business model to the application runtime.
Phase-I:
Identifies Initiatives to adopt technology innovation to prepare for startup disruption and improve the competitive landscape.
Phase-II:
Build roadmaps for Business, Applications, Systems, and Enterprise Architecture for delivering Phase-I initiatives and issues solutions.
Phase-III:
Enterprise Applications Portfolio mapping into Retire, Retain, Replace, Rehost, Replatform, and Rewrite (SixR) in alignment with the objectives established in the previous Phases.
Enterprise Applications Rationalization is a process to create business-driven application system architecture. That demands continuous input and collaboration across business, technology, and operations. We often find that enterprises lack support from business owners for the Enterprise Applications Rationalization. The Applications Disposition Strategy from applications architectures and runtimes only is a recipe for disaster down the line.
So What?
Enterprise Applications Rationalization is the mission-critical journey for any enterprise. Not doing it can put an enterprise in the same boat as Aol and Yahoo in a matter of time. The III-Phase approach enables an enterprise to stay relevant in the marketplace with the end-to-end alignment from a business model to the application runtime.
Phase-I:
Identifies Initiatives to adopt technology innovation to prepare for startup disruption and improve the competitive landscape.
Phase-II:
Build roadmaps for Business, Applications, Systems, and Enterprise Architecture for delivering Phase-I initiatives and issues solutions.
Phase-III:
Enterprise Applications Portfolio mapping into Retire, Retain, Replace, Rehost, Replatform, and Rewrite (SixR) in alignment with the objectives established in the previous Phases.
03/05: Digital BizCard
The Cloud Native Application Architecture is the leading mainstream application architecture to stay relevant for 2020 & beyond. The key business drivers for Cloud Native Application Architecture are:
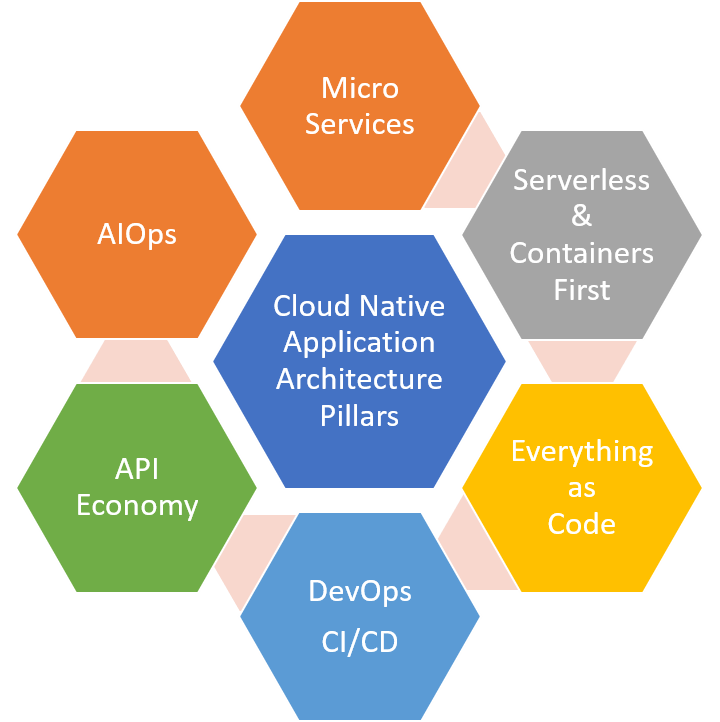
- Speed of Deployability of Everchanging Users Needs and Industry Innovation
- Economical Application Experimentation and Operations & Maintenance
- Ability to Utilize Best of Breed Technology, Platform and Framework and Adopt Next One Leading in Industry

- Micro Services - Services based application design pattern that creates end to end loosely coupled services also known as micro services to build an application. Each micro service is expected to bind by the service contract of the function it delivers at agreed performance and availability. Micro Service Owner is empowered to pick the best of breed technology, platform and framework suited for delivery of the function. Each service maintains its own independent software release cycle and run time environment for end to end autonomy. The end to end Autonomy is the key to receive true benefits of the Micro Services and may require Enterprise Architecture changes not just implementing an application utilizing fine grain services.
- Serverless & Containers First - Lightweight run time environment and/or compute resources are mission critical for successful Micro Services based Application Design and Delivery. It is cost prohibitive to live with traditional run time environments that can deliver micro services autonomy. One must think Serverless & Containers first or have business justification to pick compute deployment model otherwise as a leading practice. Enables portable deployments that are not tide to an operating system and server platform.
- Everything as Code - In other words, plug-in automation everywhere just not for software release. Mutable deployments are critical for an efficient cloud native application architecture. Package everything as code in one package for infrastructure, application run time, application deployment, testing, user acceptance, security & compliance, and monitoring to deploy and scale application services at the cloud speed economically.
- DevOps and Continuous Integration & Continuous Delivery (CI/CD) - DevOps is all about bringing end to end software release cycle under single leadership at the first line manager and automation to deliver the software to end users. This may require changes to Organization Structure and Enterprise Architecture. It is a leading practice to create CI/CD pipeline for each micro service of an application to provide Micro Services Autonomy. The first line manager now got the ownership and team with skills that can design, build, deliver and support the application service at the cloud speed.
- Application Programming Interface (API) Economy - Expose organization's digital services and assets through API in a controlled way for ease of integration between partners and applications, minimize duplication and develop & deliver new capability at the cloud speed.
- Artificial Intelligence for IT Operations (AIOps) - Use the team human resources to perform high value services then spending cycles for typical mundane task that could be automated to maintain and support your application operations. Send logs and events into a system that can analyze, learn and identify issues reactively, proactively and predictively, and has the ability to perform the resolution for the mundane repeatable tasks by augmenting intelligence to your team supporting application operations.
Disaster Recovery (DR) Deployment Models Convergence is an expected change with the innovation in Cloud and Automation. In traditional implementations, the DR deployments options are Fault Tolerant, Auto Failover, Coordinated Fail-over and Backup & Build. The Cloud Native Applications Disaster Recovery will be either Fault Tolerant or Backup & Build.
The Auto Failover will converge into Fault Tolerant and the Coordinated Fail-over will converge into Backup & Build Deployment Model(s). Any Digital transformation is incomplete without the Disaster Recovery (DR) Deployment Models Convergence.
Brief overview of the Disaster Recovery (DR) Deployment Models can be found at https://secure.baghel.com/index.php?itemid=129.
The Auto Failover will converge into Fault Tolerant and the Coordinated Fail-over will converge into Backup & Build Deployment Model(s). Any Digital transformation is incomplete without the Disaster Recovery (DR) Deployment Models Convergence.
Brief overview of the Disaster Recovery (DR) Deployment Models can be found at https://secure.baghel.com/index.php?itemid=129.
Release Automation
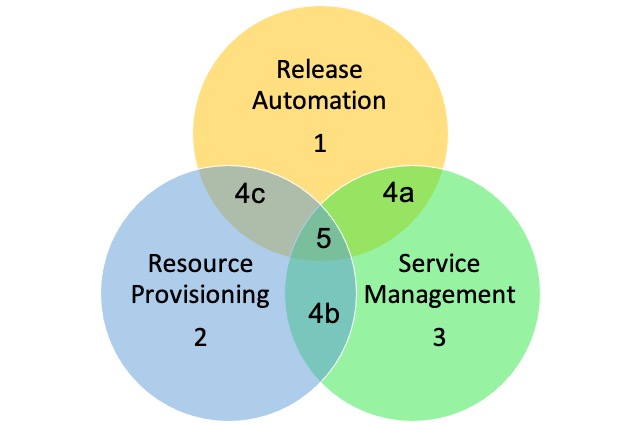
- Continuous Integration, Deployment and Delivery - Blue Green and Canary Deployment, and A/B/C Testing
- Testing Automation - Unit, QA, Performance and UAT, and Security & Compliance
- Procure and Retire of IT Services
- Baseline Builds and Configurations
- Optimization - Auto Stop, Start and Sizing
- Auto Incident, Change and Problem Resolution - AI Ops (Reactive, Proactive and Predictive)

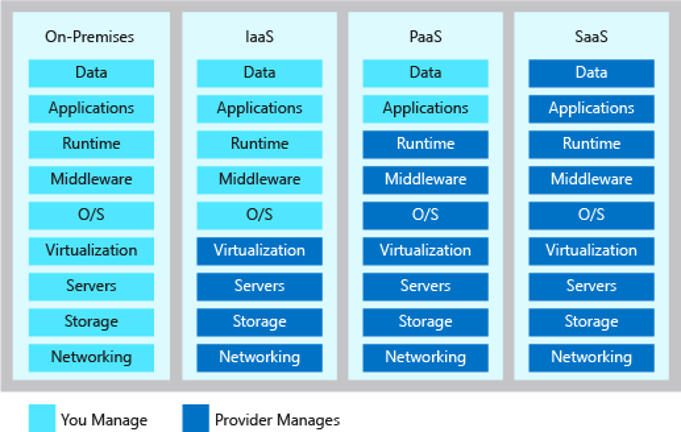
01/26: Cloud Responsibility Model
One needs to carefully plan and understand the Cloud Responsibility Model aka Shared Responsibility Model to ensure that there is no gap in the services needed to run the operations smoothly. The cloud deployments by default doesn't take over all the responsibilities and ownership necessary to run business digitally. The Cloud Responsibility Model below gives you an out of box responsibility framework for a typical deployment model types. It is a leading practice to start with out of box shared responsibility model but build a comprehensive Responsibility Assignment Matrix aka RACI with the Service Provider before going live in the new Cloud and/or Outsourcing Managed Services Model.

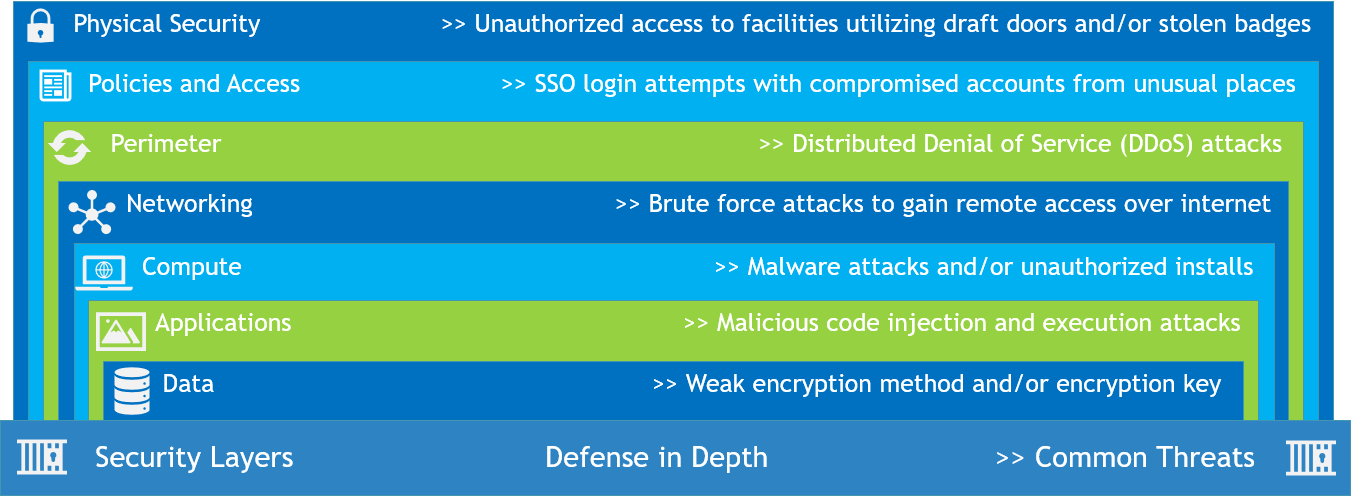
01/26: Security Layers Model
The Security Solution needs to account for the solutions for each layer described in the diagram. In specialized cases, one can assume risk but in most use cases, one should identify and implement solutions for the common threats to complete the security solution. Defense in depth is all about having security protection at multiple layers. The Security Model can serve as the point of reference when we are working on the Security Solution Design.

IP Address is also known as Internet Protocol Address. The Internet Protocol Address assignments are managed by the Internet Assigned Numbers Authority (IANA). IANA has divided the IP Addresses into two groups. First named as Public IP Address and second named as Private IP Address. The Public IP Address has to be unique in the whole world. Hence, the Public IP Address is routable to the internet. The Private IP Address is reserved to build a private network controlled by the owner of the private network without coordination with IANA and the Private IP Addresses are not unique in the world. Hence, the Private IP Addresses by default is not routable to the internet.
IANA has reserved the following IP addresses to create a Private Network:
The table provides a quick guide for sizing Virtual Networks/SubNets. The Virtual Networks and SubNets are usually configured in Classless Inter Domain Routing (CIDR) notation (x.x.x.x/8, x.x.x.x/16, ... x.x.x.x/24). The largest possible Virtual Networks/SubNets is 10.x.x.x/8 and the smallest possible Virtual Networks/SubNets is 10.x.x.x/30. It is a leading practice to consider that we keep the minimum size of the Virtual Networks/SubNets at 3x plus level. While x is the size for the proposed Virtual Networks/SubNets Go-Live requirements. Please note that hosting or Infrastructure as a Services(IaaS) provider may reserve additional IP Address in Virtual Networks/SubNets that one need to adjust and align for their Private Network Design. | 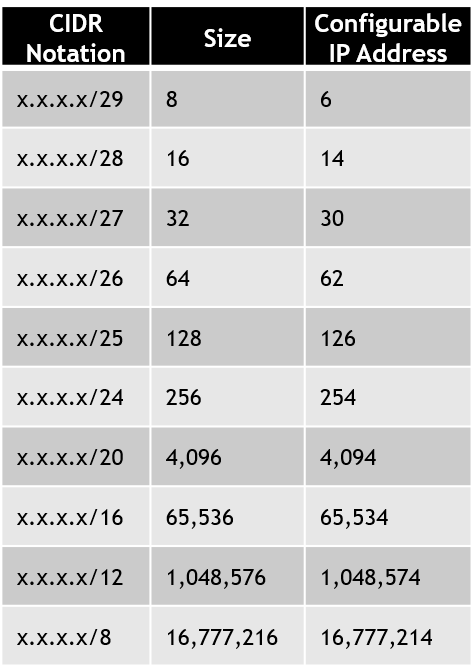 |
Disclaimer
The views expressed in the blog are those of the author and do not represent necessarily the official policy or position of any other agency, organization, employer, or company. Assumptions made in the study are not reflective of the stand of any entity other than the author. Since we are critically-thinking human beings, these views are always subject to change, revision, and rethinking without notice. While reasonable efforts have been made to obtain accurate information, the author makes no warranty, expressed or implied, as to its accuracy.


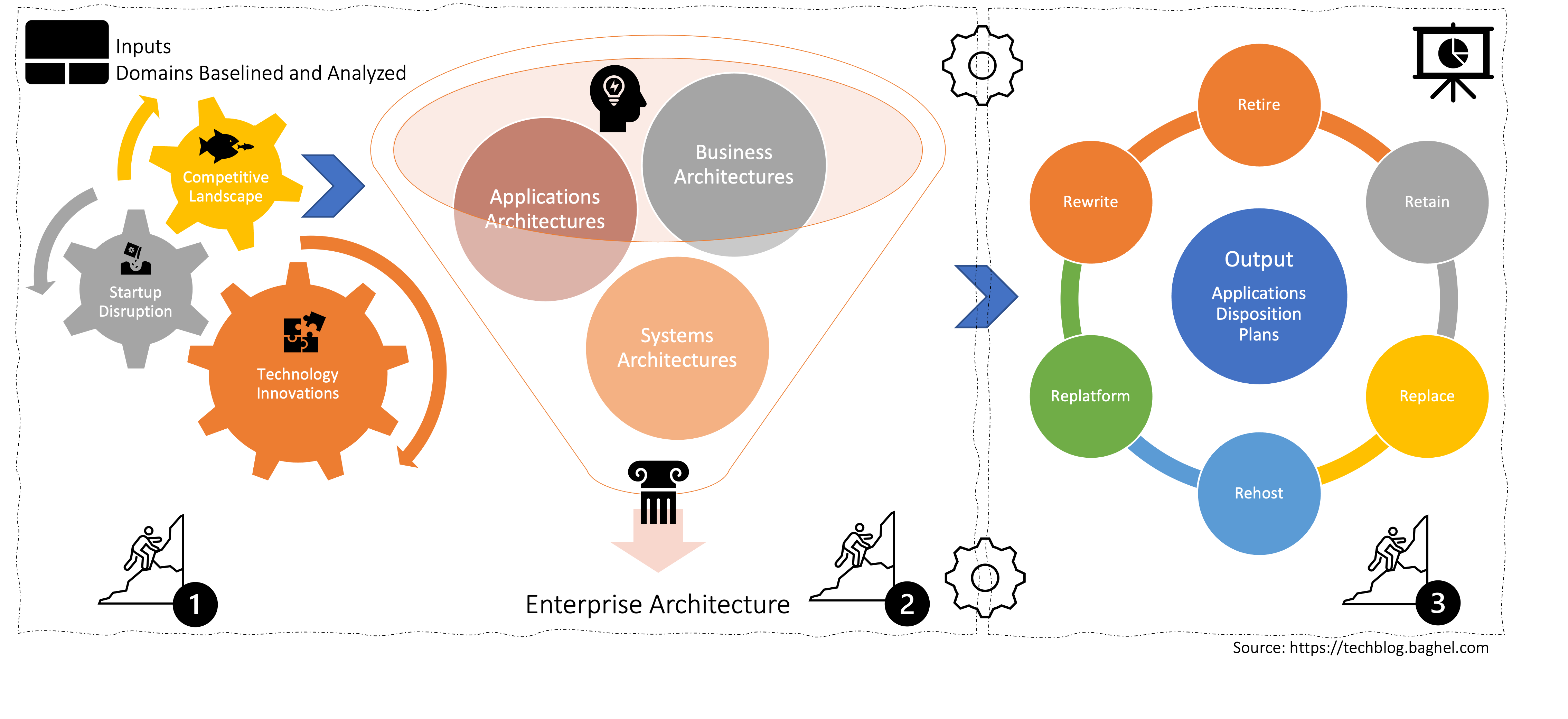 Enterprise Applications Rationalization Process
Enterprise Applications Rationalization Process