04/15: End User Monitoring (EUM)
End User Monitoring is a process of using a tool or technology that enables us to simulate a user session for define intervals and generating the performance reports for an application.
Apache JMeter usually used for Unit, Regression and Load Testing for applications, but one could leverage for EUM as well. Mercury BAC and Keynote are the commercial solutions for EUM.
Apache JMeter usually used for Unit, Regression and Load Testing for applications, but one could leverage for EUM as well. Mercury BAC and Keynote are the commercial solutions for EUM.
04/15: Why SSL?
It provides the authentication of server and optionally client identities and encrypts the data for intended recipients. One does that for one of the following reasons:
- Status Quo
- Regulatory Requirements
- Information Security
04/15: AAA Expectations
Internet Applications are expected to be Accessible Anywhere and Anytime i.e. AAA Expectations. That demands lot of discipline in design and deployment from an Internet Application.
04/15: What is a PKI?
Category: Technologies
Posted by: bagheljas
PKI stands for Public Key Infrastructure. The X.509 standard defines a PKI as "The set of hardware, software, people and procedures needed to create, manage, store, distribute and revoke certificates based on public-key cryptography." PKI has three components in its basic form:
In a typical PKI deployment, each user is assigned a pair of linked keys - a public key available to others through a CA, and a private key, which is kept secret on the user's client. A user sending a secure message uses the receiver's public key to encrypt the transmission so that only the intended recipient can read the message.
- Public/Private keys
- Digital Certificates, and
- A Certificate Authority (CA)
In a typical PKI deployment, each user is assigned a pair of linked keys - a public key available to others through a CA, and a private key, which is kept secret on the user's client. A user sending a secure message uses the receiver's public key to encrypt the transmission so that only the intended recipient can read the message.
04/15: Cryptographic Protocols
Category: Technologies
Posted by: bagheljas
- Internet Protocol Security (IPSec): IPSec is used for authenticity of two communicating hosts not users. Mostly used for building VPN and connecting a remote machine.
- Secure Socket Layer/Transport Layer Security (SSL/TLS): SSL/TLS works over TCP and tunnels other protocols using TCP, adding encryption and authentication of the server and optional authentication of client. SSL is in the process to be taken over by TLS.
- OpenPGP and S/MIME: Two competing incompatible standards for securing email.
- SSH: Used for securing remote terminals over internet
- Kerboes: Used for single sign-on and authenticates users against a central authentication and key distribution server
The basic economic values comes from SaaS are cost savings and expertise. SaaS will create an environment for people to go towards Functional Standardization. What I mean by functional standardization is that for a business function you wonít require vendor specific end user training like in today world if I know how to drive a Mercedes than I know how to drive a Honda accord. Also, we will see that lots of consolidation activity for the tasks that are cost of doing business not adding any competitive advantage for the core business.
You will find lot of product services will be created by Horizontal Integration i.e. collaborating with multiple players in the industry.
You will find lot of product services will be created by Horizontal Integration i.e. collaborating with multiple players in the industry.
04/12: Software as a Service (SaaS)
Most people think, SaaS is a web application but SaaS is an application that serves the customers over network. In today's world from a network application our expectations are that itís available 24x7x365 days and accessible from anywhere through a thin client. In short these expectations are AAA i.e. accessible any where and any time. That demands a lot of discipline in design and deploying a SaaS.
How many of you heard of Application Service Providers i.e. ASP? SaaS is nothing but an old wine in new bottle version of ASP.
How many of you heard of Application Service Providers i.e. ASP? SaaS is nothing but an old wine in new bottle version of ASP.
04/12: Operations Complexity Index
Logical Tiers (LT) >= Physical Tiers (PT)
For N Nodes in each Tier Operations Complexity Index (OCI) is calculated as
For N=4; LT=PT
3 Tier = 16, 4 Tier = 64, and 5 Tier = 256
For N=4, LT-PT=1
3 Tier = 8, 4 Tier = 32, and 5 Tier = 128
For N Nodes in each Tier Operations Complexity Index (OCI) is calculated as
OCI = (LT-PT+1)*(N^(PT-1))
For N=4; LT=PT
3 Tier = 16, 4 Tier = 64, and 5 Tier = 256
For N=4, LT-PT=1
3 Tier = 8, 4 Tier = 32, and 5 Tier = 128
Category: Best Practices
Posted by: bagheljas
Let's create some boundaries for our discussion. The best practices for Designing & Deploying SaaS are relevant for an environment where users are consuming SaaS over World Wide Web and planning to meet the AAA expectations. Address them at the design time to minimize the deployment and operations challenges.
- Optimize Software Framework & Tiers: Understand that each tier increases the operations complexity and each software library brings performance or resource overhead at the run time. Hardware is cheap but running that host is not. So, keeping two logical tiers on a physical tier provide savings in multiple areas and specially reducing the operations complexity. As you see in 4 tier architecture by just combining two logical tiers over one physical tier it cuts the operations complexity into half and dropping an entire tier drives your operations towards simplicity.
- Security & Service Level Agreements: Start with locking down every thing from network or host perspective and open only what needs to be open. Itís very difficult to implement firewalls at later stage. Use SSL offload as much as possible as L4 switches providing these capability are highly optimized for it than application servers. If you are B2B and B2G consider allowing traffic by 2 way SSL to minimize the hacking/cracking risk. Implement Open Source Web Application Firewall that protects you from the known hacking/cracking activities and gives you an ability to quickly block new vulnerabilities by signatures. Understand the SLA of availability & load and make sure to set rate limiting or throttling as if you agreed to accept 100000 requests per day but didnít understand what comes every min, may break your system. Set parameters for your developers like under 600ms for a web page to render and under 200ms to tcp/rmi calls. This is important to set early enough to make right decision for software design and provides an opportunity to scale economically in production. Service level expectations are something that your clients legally canít take actions against you but will use them against you at the time of renewals. So, understand them and have room in your design & deployment to meet these expections to keep the customer happy.
- Load Sharing and DNS TTL Settings: The word load sharing is confusing as most tools either load balance by users or requests not by actual pay load created by them. As we are multi site at minimum we have implemented the DNS rotor kind of solution that round robins the traffic between your sites. GSLB is dynamically routes the traffic based on the availability health checks of your sites. If a site is down, it automatically keeps that site out of rotation. Implementing GSLB in-house vs. outsourced. Consider the fact that what business values it has for you. If your data centers are 20 miles apart and outsourced solution like Akamai gives you health checks and user mapping to site based on distance is not useful for your model. Understand the business value and make a decision. On L4 VIPs, I like to use Round Robin and Least Connection load sharing algorithm. These both will perform at the same level for http and https traffic but for tcp/rmi traffic least connection performs better than Round Robin. Most L4 VIPs default config is Round Robin. You are multi site, so you need to make sure that your DNS cache expires immediately or max time to live i.e. DNS TTL is set to 120 seconds. Otherwise, when you bring a site out of rotation, users will experience a bad behavior of non-availability.
- Forward vs. Backward Compatibility: Understand the business and the market you are in and make a choice between Forward and Backward Compatibility. If your business model can sustain than design your SaaS with forward compatibility compare to backward compatibility for higher profitability. As we operate businesses for profitability not for revenue.
- Coupled vs. Decoupled Interfaces: Letís first understand, what I mean by coupled vs. decoupled interfaces. In a horizontal integration environment when a change in lower stack needs corresponding change in upper stack, then they are operating under coupled interfaces. If not, than they are operating under decoupled interfaces. Create coupled interfaces only if itís creating a business value for you otherwise create decoupled interfaces so both parties can innovate independently. Coupled interfaces have high maintenance cost compare to de-coupled interfaces.
- Synchronous vs. Asynchronous: In a transaction in real life we create lot of logging events for various monitoring and reporting activities. It is a good practice to spin a new independent thread for logging events. That helps perform better compare to same thread needs to complete everything. Mostly batch jobs creates problems for real time end user activities, itís a good practice to invest into a miniature environment for batch jobs to avoid performance issues. Only real time response activities should use Synchronous communication.
- Stateful vs. Stateless: World Wide Web is stateless and see if your design can support that for deployment & operations simplicity. For performance reason, if you need Stateful and if your user is routed from server A to server B and there is no end user impacts other than it takes little longer to serve the customer. You are still ok. But, if your application functionality breaks without Stateful setup than implement application server clustering solutions and donít create more than three nodes in a cluster as bigger size cluster adds overhead than any added benefits to it.
04/12: Operationability
Its all about making technical decision(s) to create business value while minimizing the operations complexity and issues to make the IT solutions and services financially viable to you and your clients.
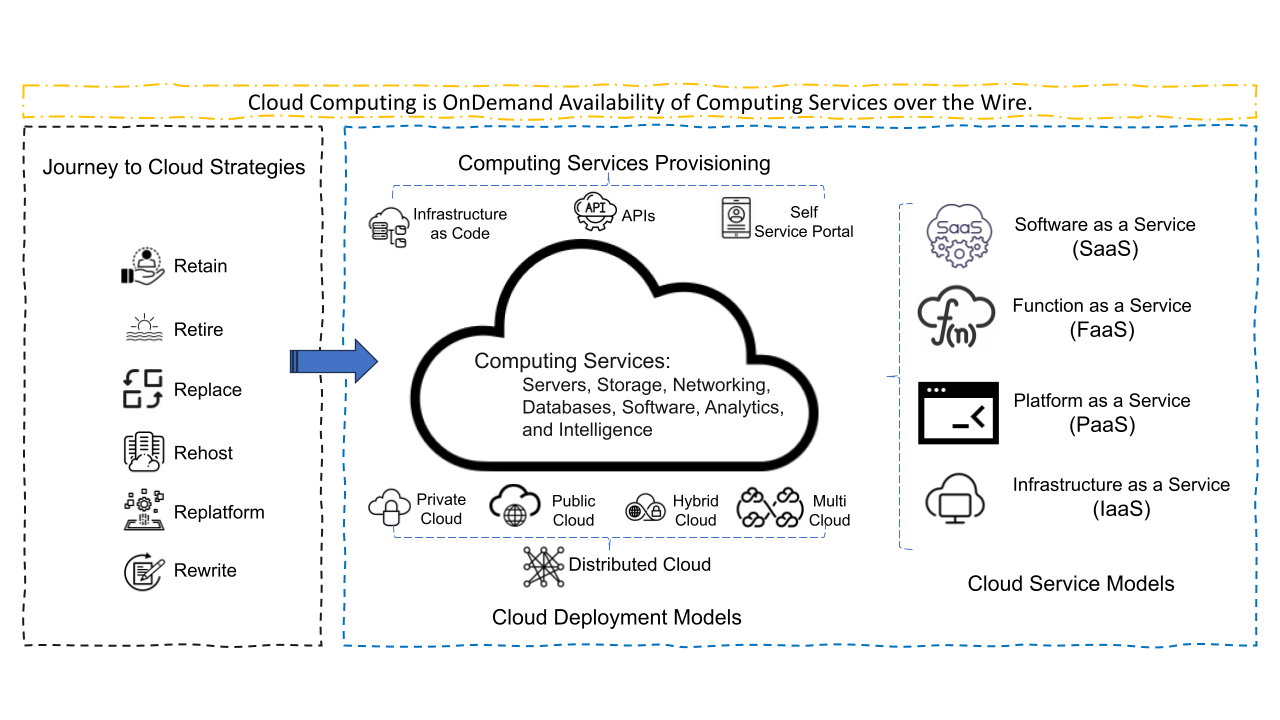
04/12: Cloud Computing
Cloud Computing is OnDemand Availability of Computing Services over the Wire. Cloud Computing's foundation is the virtualization and provisioning of computing services using APIs, Infrastructure as Code(IaC), or Self Service Portals. Cloud Computing has Infrastructure as a Service (IaaS), Platform as a Service (PaaS), Function as a Service(FaaS), and Software as a Service (SaaS) as its service building blocks.
Disclaimer
The views expressed in the blog are those of the author and do not represent necessarily the official policy or position of any other agency, organization, employer, or company. Assumptions made in the study are not reflective of the stand of any entity other than the author. Since we are critically-thinking human beings, these views are always subject to change, revision, and rethinking without notice. While reasonable efforts have been made to obtain accurate information, the author makes no warranty, expressed or implied, as to its accuracy.
The views expressed in the blog are those of the author and do not represent necessarily the official policy or position of any other agency, organization, employer, or company. Assumptions made in the study are not reflective of the stand of any entity other than the author. Since we are critically-thinking human beings, these views are always subject to change, revision, and rethinking without notice. While reasonable efforts have been made to obtain accurate information, the author makes no warranty, expressed or implied, as to its accuracy.